3. Hardeing SSH Access
Now that you've setup a non-root user with key-based authentication and sudo privileges, it is time to harden the ssh access. This will result in a few things:
- Default SSH-port will be changed from 22 to 69 or 60483. This will prevent automated scripts from being able to target your machine
- Disabling root user login via SSH. The only user who will be able to login via ssh, will be the non-root user you created. Again, this will protect you from automated scripts that have a default user of
root - Disabling Password Authentication: Basically, you will not be able to login into the server with your password. Disables all password-based authentication via ssh. You won't be able to login without the private key.
By undertaking all these measures, you secure your server from unauthorised access.
Remember, all this is useless if someone else gets their hands on the private key file
In order to set up these security measures, you need to edit the ssh configuration file located in /etc/ssh/sshd_config on the host machine. You can either ssh into it and then edit the file or edit it directly on the display output of the machine.
I would recommend using a text editor called nano. It is very simple to use.
cd /etc/ssh/
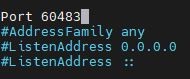
nano sshd_configThis will open a text editor in the Terminal. Using arrow keys scroll down until you see Port 22.
Change this to Port 69 or Port 60483.
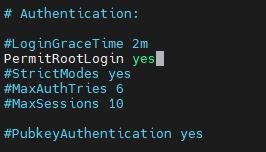
Next, Scroll Down a little further until you see PermitRootLogin yes
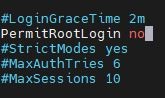
Change PermitRootLogin yes to PermitRootLogin no
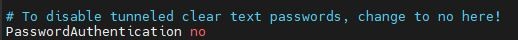
Next scroll down using arrow keys until you find PasswordAuthentication yes and change it to PasswordAuthentication no
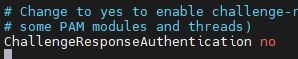
Also add ChallengeResponseAuthentication no, at the bottom of the text file
Now that you have editted everything you needed to, it is time to save and exit the file. Press Ctrl + X, y, Enter.
You now need to restart the ssh service on the host machine to enforce the changes we have made. For this, run:
sudo systemctl restart sshdNow, open another terminal window on your client machine and enter the following:
cd
ssh -i ./.ssh/id_rsa -p 60843 username(@)192.168.1.255Breakdown of commands:
cdchanges your current working directory to/home/{your-username}on the client linux machinesshis ssh (LOL)-iattribute states the location of the private key file-pattributes the network port to use for ssh connection. By default it is22but as we changed it on host machine, we need to manually set the port as60483
And you should now see your ssh terminal! Your server's ssh access has now been hardened!

No comments to display
No comments to display